We have just recently migrated to single-factor-auth@6.5.0 (just saw that 7.0.0 was published yesterday).
We Implemented a very simple setup:
On Web3auth’s end we have an aggregate verifier, and we login using Auth0. Once logged in we then pass the id_token to the SDK like so:
const web3AuthProvider = !sessionId
? await web3Auth.connect({
verifier: Web3AuthDeps.socialVerifierName,
verifierId: session.user.email,
idToken: idToken,
subVerifierInfoArray: [
{
verifier: session.user.loginProvider,
idToken,
},
],
})
: web3Auth.provider
This setup works, all variables you see here are accounted for and correct.
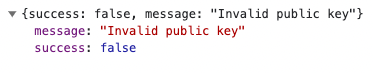
However - I noticed from our logs that sometimes web3Auth.sessionId has a value, but web3Auth.provider is null. This is directly correlated to an API call I can see happening in the background. The call is made to https://broadcast-server.tor.us/store/get with a query param called key. When this call fails (image attached), the provider isn’t available. For example:
I logged in before I started writing this post. The provider was available and the API call was successful. I refreshed the page just now, the call fails and the provider is null.
This isn’t something we can rely on in production, please advise
Failed request:
Response when fails:
The API request as cURL, this is reproduced also when just running this in the terminal (I can see the response changes):
curl 'https://broadcast-server.tor.us/store/get?key=04afffb4962f29d7e68b0410ebdabea19649a598c298b845629dd302a96959caeae4bee6314661fd7a14e76047466758a473b9a3411a27ef7b2386b4e92761f4f1' \
-H 'authority: broadcast-server.tor.us' \
-H 'accept: */*' \
-H 'accept-language: en-US,en;q=0.9' \
-H 'origin: https://app.grappa.xyz' \
-H 'referer: https://app.grappa.xyz/' \
-H 'sec-ch-ua: "Chromium";v="116", "Not)A;Brand";v="24", "Google Chrome";v="116"' \
-H 'sec-ch-ua-mobile: ?0' \
-H 'sec-ch-ua-platform: "macOS"' \
-H 'sec-fetch-dest: empty' \
-H 'sec-fetch-mode: cors' \
-H 'sec-fetch-site: cross-site' \
-H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/116.0.0.0 Safari/537.36' \
--compressed
